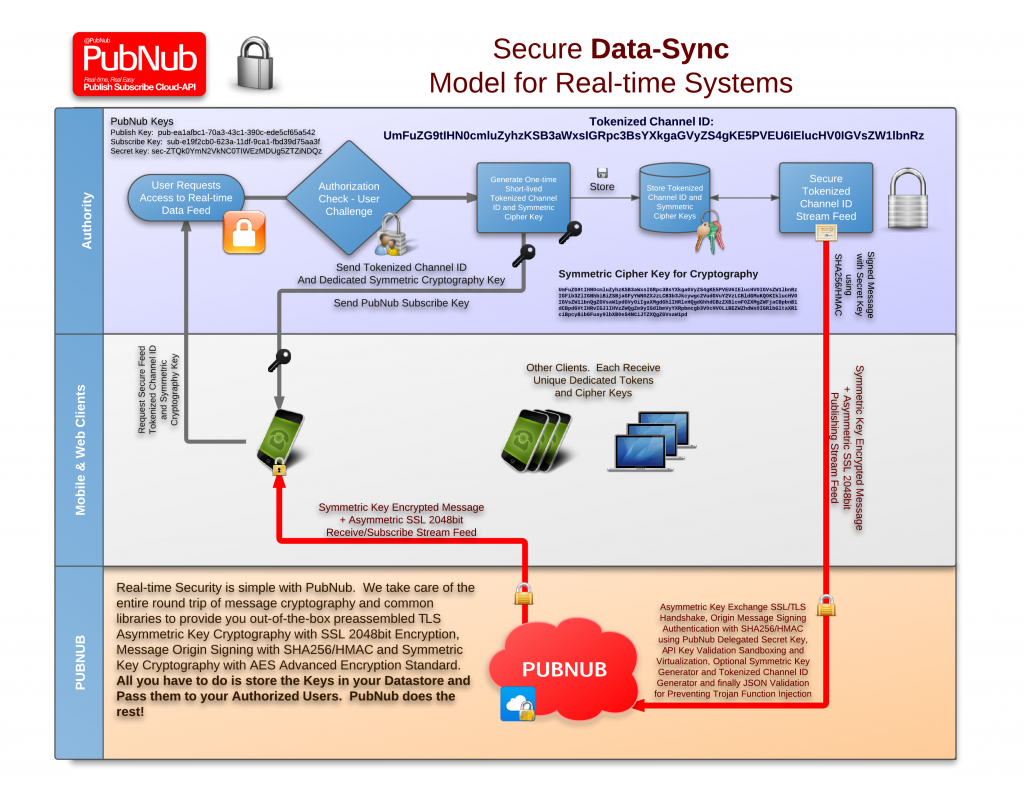
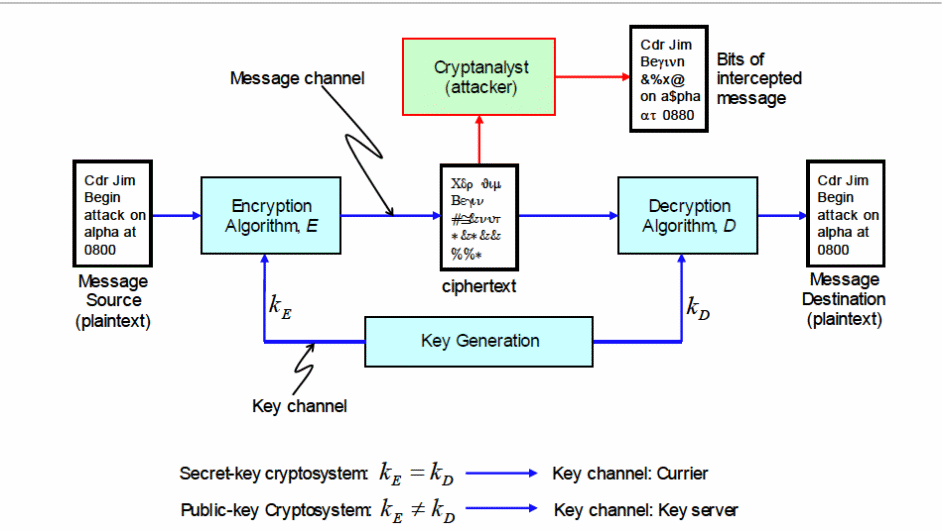
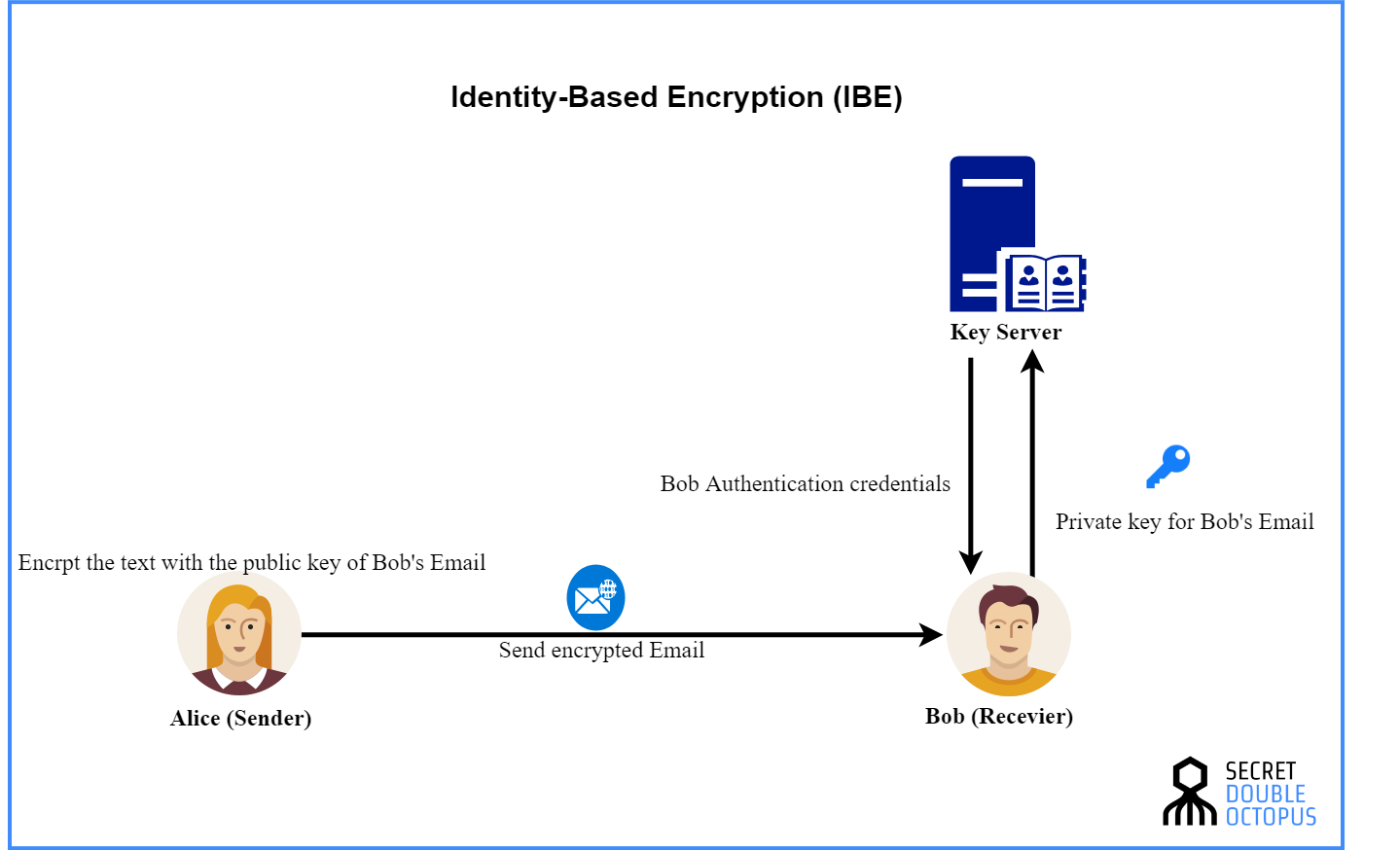
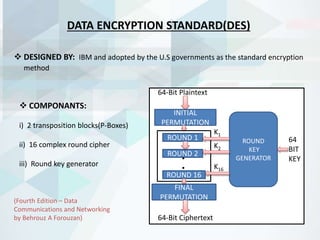
Securing color image transmission using compression-encryption model with dynamic key generator and efficient symmetric key distribution | Semantic Scholar

Securing color image transmission using compression-encryption model with dynamic key generator and efficient symmetric key distribution | Semantic Scholar
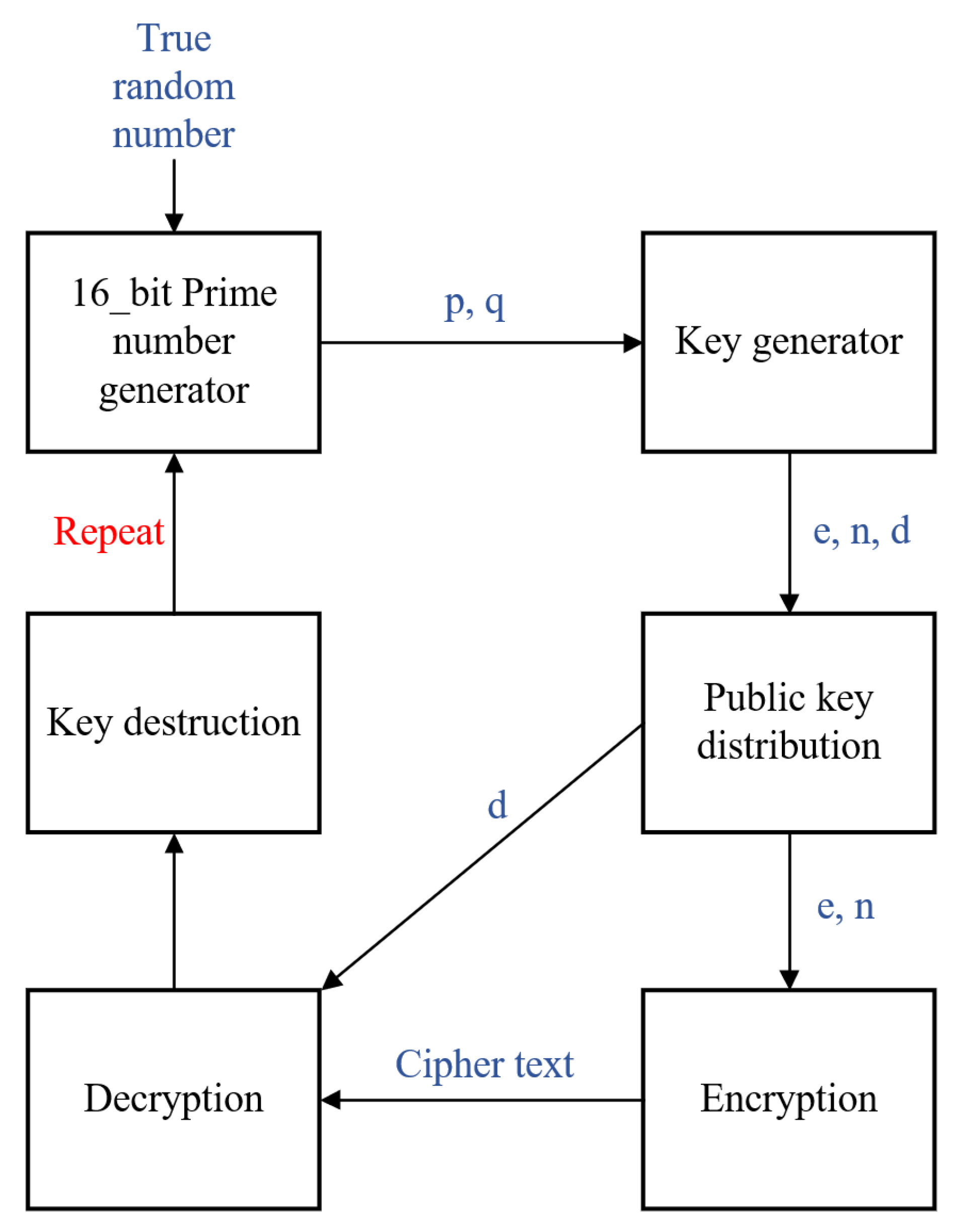
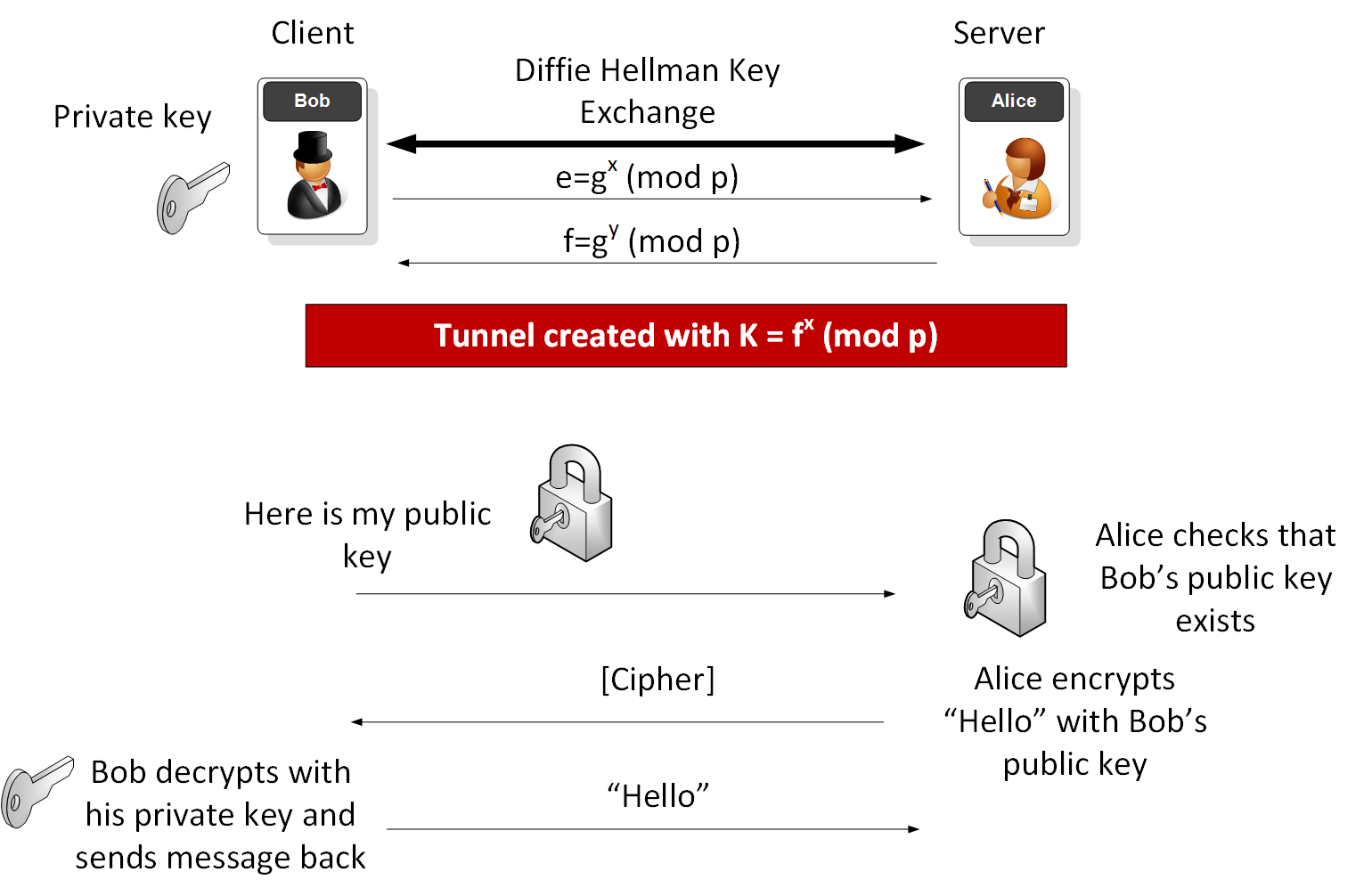
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices

Applied Sciences | Free Full-Text | Block Data Record-Based Dynamic Encryption Key Generation Method for Security between Devices in Low Power Wireless Communication Environment of IoT
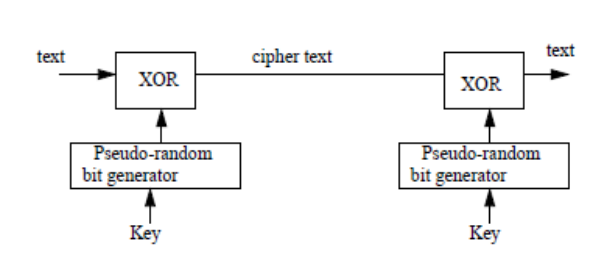
Symmetric-key encryption schemes. (a) Stream cipher using algorithmic... | Download Scientific Diagram






![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/symmetric%20crytography%20opt.jpg?width=1002&name=symmetric%20crytography%20opt.jpg)